How to do Risk Analysis?
All software projects benefits from risk analysis. Even non-critical software, using risk analysis at the beginning of a project highlights the potential problem areas. This helps developers and managers to mitigate the risks. The tester uses the results of risk analysis to select the most crucial tests.
How Risk Analysis is done?
Risk analysis is a well-defined process that prioritizes modules for testing.
A risk contains following three components
(a) The risk (rI) associated with a project (i <- 1 to n).
(b) The probability of occurrence of a risk, (II).
(c) The impact of the risk (XI)
Risk analysis consists of first listing the potential problems and then assigning a probability and
severity value for each identified problem. By ranking the results, the tester can identify the potential problems most in need of the immediate attention and select test cases to address those needs.
There are two methods of doing systematic risk analysis
Method-1: Using Risk Analysis Table (RAT)
| Problem ID | Potential Problem (rI) | Probability of
occurrence(II) |
Impact of
Risk (xI) |
Risk Exposure =(II) * (xI) |
| A | Loss of power | 1 | 10 | 10 |
| B | Corrupt file header | 2 | 1 | 2 |
| C | Unauthorized access | 6 | 8 | 48 |
| D | Databases not synchronized | 3 | 5 | 15 |
| E | Unclear user documentation | 9 | 1 | 9 |
| F | Lost sales | 1 | 8 | 8 |
| G | Slow throughput | 5 | 3 | 15 |
Legend for the Risk Analysis Table is as under
Problem ID: Is a unique identifier associated with a risk.
Potential problem (rI): It is a brief description of the problem.
Probability of occurrence (II): It is a probability value on a scale of 1 (low) to 10 (high).
Severity of impact (XI): It is a severity value on a scale of 1 (low) to 10 (high).
Risk exposure: It is defined as the product of (II) and (XI).
In this Risk Analysis Table, the values of II and xI range from 1 to 10.
Multiplying the probability and severity values yields the risk exposure.
“The higher the risk exposure product, the more important it is to test for that condition”.
Applying this rule to the above Risk Analysis Table, we will get the following rankings of the potential risks problems based on the product of risk-exposure.
The order of preference shall become
C-D-G-A-E-F-B
Although problems D and G have the same risk exposure, they differ by their probability and severity values.
Some organizations prefer to use this method of using Risk Analysis Table, while many others adopt risk-matrix analysis methodology.
Method-2: Risk Matrix Analysis (RMA)
A risk matrix allows the tester to evaluate and rank potential problems by giving more weight to the probability or severity value as necessary. The software tester uses the risk matrix to assign thresholds that classify the potential problems into priority categories.
There are four main methods of forming risk matrices
RMA Method – 1: Typically, the risk matrix contains four quadrants, as shown below.
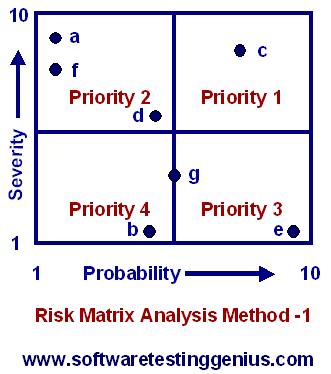
Each quadrant in the above figure represents a priority class defined as under
Priority 1: High severity and high probability.
Priority 2: High severity and low probability.
Priority 3: Low severity and high probability.
Priority 4: Low severity and low probability.
We can see from the graph of above figure that a risk with high severity is deemed more important
than a problem with high probability. Thus, all risks mapped in the upper left quadrant fall into priority 2.
For example, the risk-e, which has high probability of occurrence but low severity of impact, is put under priority 3.
RMA Method – 2: For an entirely different w application, we may swap the definitions of priorities 2 and 3, as shown the figure below.
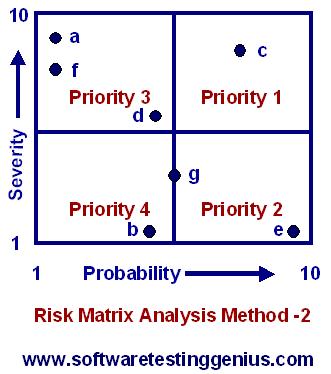
An organization favoring the above figure seeks to minimize the total number of defects by focusing on problems with a high probability of occurrence.
Dividing a risk matrix into quadrants is most common. The testers can determine the thresholds using different types of boundaries based on application specific needs.
RMA Method – 3: Diagonal band prioritization scheme.
If severity and probability tend to be equal weight i.e., if (II) = (XI)., then diagonal band prioritization scheme may be more appropriate. This is shown in the figure given below.
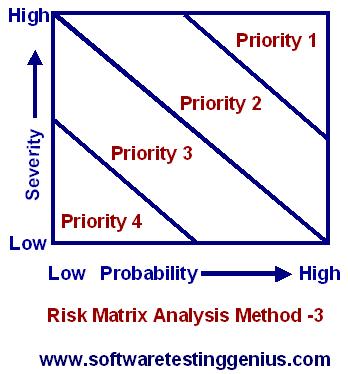
This threshold pattern is a compromise for those who have difficulty in selecting between priority-2 and priority-3 in the quadrant scheme.
RMA Method – 4: Some managers found out that the problems with high severity must be given the top priority, irrespective of the value of probability. This problem is solved with RMA Method-4 and is shown in following figure.
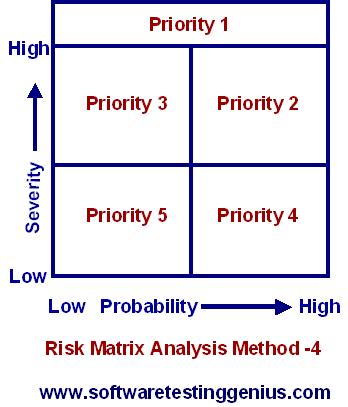
The remainder of the risk matrix is partitioned into several lower priorities, either as quadrants (RMA Method-1 and 2) or as diagonal bands (RMA Method-3).
Many More Articles on Risk Analysis & Security Testing

An expert on R&D, Online Training and Publishing. He is M.Tech. (Honours) and is a part of the STG team since inception.

cool post! Keep up the neat work!